Post by ProBoards Help Guide on Apr 22, 2013 15:50:20 GMT -8
The security log is an important tool for monitoring activity on your forum. Any content on your forum that has been deleted or modified and any staff powers that have been used will be logged here.
To view your forum's security log visit the admin area of your forum and select Security. On the following menu, select Security Log.
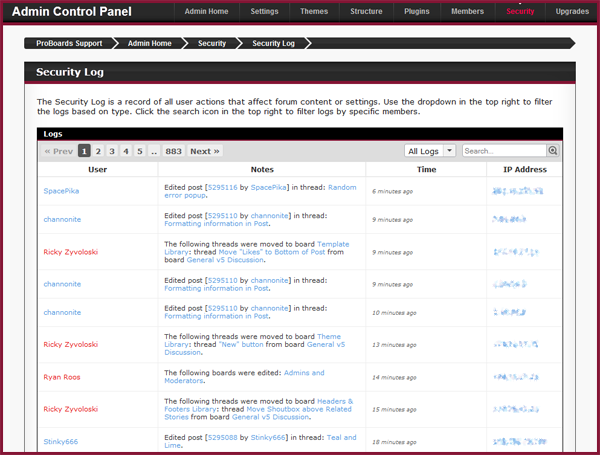
Actions tracked in the security log will be sorted with the following information:
The pagination bar at the top of the logs allows you to:
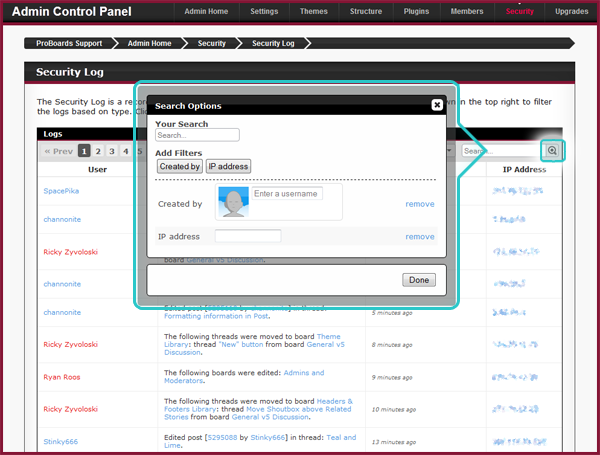
The security log filters are as follows:

Each security log filtering category can be clicked, but also has even more precise filters inside the category to show logs related to very specific actions relating to the category.
Source: www.proboards.com/admin-guide/security/security-log
To view your forum's security log visit the admin area of your forum and select Security. On the following menu, select Security Log.

Actions tracked in the security log will be sorted with the following information:
- User — The member on your forum that performed the action.
- Notes — An explanation of the action the member took and links relating to the page the action affected.
- Time — The time the action took place. Hovering your mouse over the timestamp will provide you with the exact time the action took place down to the second.
- IP Address — The IP address associated with the action. Clicking on the IP address will give you the option to ban the member if necessary.
The pagination bar at the top of the logs allows you to:
- switch between each page of the logs.
- search for logs made by specific IP addresses or members of the forum. To do this, click the search (magnifying glass) icon.
- filter the logs based on what kind of action was taken.

The security log filters are as follows:
- All Logs — Every security log entry on the forum.
- Admin Logs — Actions taken relating to admin area functionality.
- Board Logs — Actions taken relating to board management and reorganization.
- Category Logs — Actions taken relating to category management and reorganization.
- Conversation Logs — List of times a member has deleted a conversation.
- Custom Page Logs — List of changes made to any of your forum's custom pages.
- Group Logs — Changes made to any of your member groups, as well as new groups added.
- Member Logs — Changes made to member profiles by anyone on the forum.
- Plugin Logs — Modifications done to any of your plugins' settings or building components.
- Post Logs — List of deletions and edits made to posts by members and staff, as well as logs of when a post was moved out of a thread.
- Reported Posts — List of reported posts and actions your forum's staff has performed on those reports.
- Theme Logs — List of recent changes made to any of your forum's themes.
- Thread Logs — List of threads which had any moderator actions performed on them, as well as polls and events added to threads.

Each security log filtering category can be clicked, but also has even more precise filters inside the category to show logs related to very specific actions relating to the category.
Source: www.proboards.com/admin-guide/security/security-log






